
Continuing the Security Tips series I started in July '13, today I wish to discuss with you all the topics listed after the following links. Just in case you want to access the last posts in this series, here are the links:
Part 1: General Guidelines - Click Here
Part 2: Microsoft Windows - Click Here
Part 3: Macintosh - Click Here
Part 4: Guest Accounts - Click Here
Part 5: Windows Firewall - Click Here
Part 6: Event Viewer & Netstat - Click Here
Let's first consider in brief the structure of this post.
- Introduction
- Need for Antivirus Program
- How does Antivirus Software work?
- Some popular Antivirus Software
- Choosing the Best Antivirus Software
- Steps to Install Antivirus
- How to test if Antivirus is not working
- Configuring McAfee Antivirus (Scanning & Scheduling)
- Configuring Kaspersky PURE (Parental Control & SafeMoney)
- Configuring Avast! Antivirus (Added utilities)
- Configuring BitDefender Antivirus (Firewall & Wallet)
- Conclusion/Comments
In the configuring antivirus topics, I would discuss configuration of an antivirus software in detail. For different options I’ll use different antivirus software. Since one kind of option is almost similar for all these, so I thought to discuss different features on different antivirus to make you feel confortable with interface of most of them.
Introduction
A computer connected to the Internet is always at high risk, and it is always recommended to install antivirus software onto the system. Get it? Always remember you are never 100% secure! A computer virus can degrade the performance of a computer and delete stored computer data. Viruses usually spread through networks by means of download, emails, shared disks, and due to browsing a lot of ‘unmentionable-content’ (get it? :P). If an infected file is attached to these sources, then the system is likely to become infected upon opening the infected files. Some of the symptoms indicating viral infection are improper functioning of applications, slow operation, an unusual error message, frequent hanging, frequent-restarting, problem printing, double extension on any attachment, and distorted menus and dialog boxes, and BLAH! BLAH! BLAH! You know this stuff guys!

An antivirus program scans the hard drive, optical drives, floppy disks (LOL! Do they exist yet? :P), removable media, etc. etc. etc.!!! PHEW! Oh I was saying it scans all that to protect your computer against viruses, worms, spyware, Trojans, and more. It ensures that the system is healthy and alerts the person to implement safety measures against harmful attacks. Regularly update the antivirus software by subscribing to the updates from antivirus vendors whenever offered. The virus dictionary and suspicious behaviour approaches are the most widely used approaches by antivirus software to detect malware.
Now that was a long Introduction! Let’s get deeper into the discussion.
Need for Antivirus Program
Today in the digital domain, loads of data is stored on computers and it has become significant to protect the data. When a PC is connected to the Internet the PC has to combat various and different types of malware programs (I have discussed different types of malware in my earlier posts). Cyber criminals such as attackers and hackers use these malicious programs as tools to steal important information such as personal data stored on the computer. These programs pose a severe threat to the computer and may destroy its functionality in different ways.
Malicious programs pave their way into one’s PC through email attachments and spam email, through USB drives, visiting fraudulent websites, etc. Due to the invasion of malicious programs in cyberspace, antivirus programs have become necessary for computers. If your computer has a good antivirus program installed on it then it is protected against and can combat most of the malware.
How does Antivirus Software work?
There are two common techniques used by antivirus software for virus detection, or rather ‘suspicious file detection’ to be more precise since they are known to show certain false positives. These two are:
- Virus Dictionary: To look for some known virus
- While examining files, the antivirus software refers to the virus dictionary which is created by the antivirus creators
- If certain snippet in the code is equivalent to that in any virus, it is considered malware of that virus kind
- It is necessary that this dictionary is always up to date
- On-access protection implies the file will be scanned every time any user/daemon process access that file.
- Scheduled scans are quite successful in reducing the risks
- Suspicious Behaviour: To examine any suspicious behaviour as shown by malware
- In this approach, the antivirus software monitors the behaviour of all programs instead of identifying the known viruses
- Whenever a program with suspicious behaviour is found, the software alerts the user and asks what to do
- This is better in identifying new and unknown viruses
- Other techniques:
- Anti-virus software will try to emulate the beginning of each new executable code that is being executed before transferring control to the executable
- If the program seems to be a malware/self-replicating/self-modifying code, then it immediately examines the other executables
- Much more false positives are thus detected
- Sandbox emulates the host OS and runs all executable (generally suspicious ones) in an inert environment for execution. The sandbox is examined for viruses after the program terminates.
Some popular Antivirus Software

Choosing the Best Antivirus Software
When purchasing an antivirus software, look for certain features and choose the one that can best serve your needs.
The most important things to consider are:
- Antivirus Scanning
- Antivirus Detection Accuracy: Ensure that antivirus scans and detects viruses accurately and detects majority of threats
- Scanning Speed: Ensure that the antivirus software can perform the task quickly and efficiently
- Resource Utilization: Ensure that the antivirus software utilizes minimal resources and does not affect system performance when scanning the computer
- Hacker Blocking: Prevents other users from gaining unauthorized access and stealing important data such as passwords and other confidential information
- Bidirectional Firewall: Ensure that the antivirus software is equipped with a software firewall to scan both incoming and outgoing traffic
- Technical Support: Look for good technical support so issues can be solved easily
- Parental Controls: Ensure that the antivirus program has parental control features so children can browse the Internet safely
- Easy Installation & Use: The software should be user-friendly and easy to use
- On-demand and scheduled scanning: Allows you to schedule a scan according to a user-specified time. Users can schedule the scan daily, weekly, or monthly
- Automatic Updates: keeps the user abreast of the latest online threats without the user having to visit the vendor’s website time and again
- Spyware detection and prevention: Checks for antispyware components keeping spyware at bay
- Email scanning: Email protection can monitor POP and SMTP ports and ensure that the emails do not contain a threat to your computer
Steps to Install Antivirus
Most of the antivirus software use an install wizard which is quite easy to follow. I think I should not discuss this in more detail, since I have already talked about installing avast! and eset earlier.
How to test if Antivirus is not working
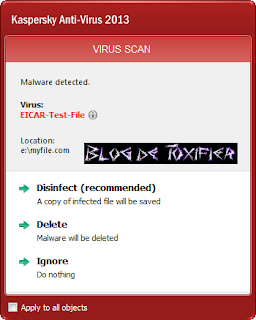
To determine the presence of consistent virus protection, follow these steps:
- Open a new document in Notepad
- Copy the following code into it, and save the file.
X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*
- Rename the file as myfile.com
- Run the antivirus scan on myfile.com
- If the antivirus is functioning properly, it will generate a warning and immediately delete the file.

Configuring McAfee Antivirus (Scanning & Scheduling)
First I am sharing pics of how to install McAfee Antivirus:
Okay, done? Now let’s continue with its configuration:
- On the main Security Centre console, click Schedule and run scans, and select scan you PC.
+1.png)
+2.png)
- After selecting, Scan your PC, select any one of the available scan types. This initial scanning of computer as soon as we install an antivirus is recommended to make sure our system is clean.
+3.png)
+4.png)
- Done with the initial scans? Now let’s schedule some scans. So again, on the main Security Centre console, click Schedule and run scans, and select Schedule scans
+1.png)
+2.png)
- Now select some sensible values. Why I say that? The recommended ones Friday, 04 am, etc. are totally ridiculous! So make sure you select some days and time combination when your PC is actually ON in order to get a scan done.
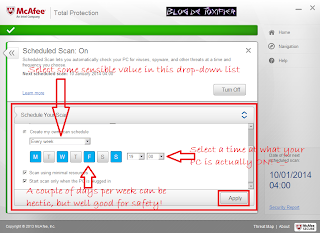+3.png)
Configuring Kaspersky PURE (Parental Control & SafeMoney)
First let’s talk about the installation process, nothing big really, but I am sharing screenshots, okay?
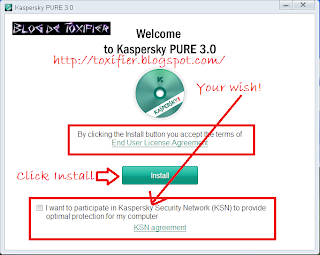

Done with the installation, now let’s see how to configure Parental Control in Kaspersky PURE.
- SafeMoney: It is a handy tool that prevents the burden of entering important bank information at ecommerce websites again and again by securely saving it in an encrypted vault. This also prevents any eavesdropper from seeing your information, which can be seamlessly entered into the website using SafeMoney
- Parental Control: Another great tool to keep your children safe online. Do configure it if you have a family where you wish to impose certain restrictions on other people using your computer.
- Click on parental control tab on the right side of the main window

- Setup a password to secure your settings from modifications. Also mention what all settings you wish to safeguard using the password


- Select a computer user to impose restrictions on by clicking the Select control level button beside the username

- Select a level control if you wish to use a predefined one, or click on Custom Restrictions and settings button to make some custom restrictions

- Make whatever settings you wish to make for a number of issues you can see in the window that opens. Save and apply changes.

- Click on parental control tab on the right side of the main window
Configuring Avast! Antivirus (Added Utilities)
For installation and review of avast! antivirus, consider this link: http://toxifier.blogspot.com/2013/09/the-best-free-antivirus-avast-review.html
Now let’s talk about configuration part.
There are various added features provided by most vendors. Avast! provides some really common and cool ones. I’ll discuss them here.
- Browser Cleanup: This tools help you get rid of damn cookies, some ‘ahem-ahem’ history traces, idiotic toolbars, and all other browser level crap! Click Tools, select Browser Cleanup. Click start Browser Cleanup. After analysis is complete select your browser to reset.
.png)
.png)
.png)
- Secure Line: This is a VPN service provided by avast! It is really cool. If you’d like to spend a little money, do check this out :)
.png)
- Software Updater: This is a utility that helps you check for updates of all the monitored software which include browsers, plugins, windows updates, etc.
.png)
- Access Anywhere: This is used to remote control your device
.png)
- Rescue Disk: This is an awesome feature, to save state of your computer to recover back to if you bring upon some disaster on your PC!
.png)
Configuring BitDefender Antivirus (Firewall & Wallet)
- Firewall: Firewall is a great tool. I have already discussed Windows Firewall earlier here: http://toxifier.blogspot.com/2013/08/guidelines-for-securing-operating_20.html
- Wallet
This tool helps a lot for those with personal computer. You can store important credentials like email account passwords, etc. in the wallet for fats, easy, and secure access.
Conclusion/Comments
I hope you find all the relevant information you must know about the topic of security I discussed with you all today. For any queries or suggestions please feel free to comment here.
Just click the image below to download avast! for free Don’t worry it is completely legal, free and safe to use!

I hope you all have a great day ahead! :) Happy Tuesday! :) See you all soon! :D That was a very very long post! I am going to sleep now! zzzzzzzzzzzzz



.png)
.png)
.png)
.png)
.png)
.png)
.png)
Hi Toxifier, having previously used the Kaperski antivirus, but very expensive for us because we operate three machines in our homes. Most free programs are up to machines, Panda Cloud Antivirus, Panda coud Cleaner, IObit Malware Fighter, Advanced SystemCared 1.7 Pro coexist, there is no problem with them, yesterday I downloaded the Stinger program that recognizes and removes more than 6000 virus if the computer is on, thank your offer friendly greetings Aniko
ReplyDeleteI see. You can try avast! I have shared it's download link in the image at the end of this post :)
DeleteGreeat post thankyou
ReplyDelete