
Continuing the Security Tips series I started in July '13, today I wish to discuss with you all the topics listed after the following links. Just in case you want to access the last posts in this series, here are the links:
Part 1: General Guidelines - Click Here
Part 2: Microsoft Windows - Click Here
Part 3: Macintosh - Click Here
Part 4: Guest Accounts - Click Here
Part 5: Windows Firewall - Click Here
Part 6: Event Viewer & Netstat - Click Here
Part 7: Antiviruses - Click Here
Part 8: Data Encryption - Click Here
Let's first consider in brief the structure of this post.
- Introduction
- Cryptography Tools
- TrueCrypt
- Conclusion/Comments
Since my last post was quite long, so I decided to discuss Cryptography Tools and TrueCrypt in this post. So here you go! :)
Introduction
Personal computers and portable computing devices often contain confidential data such as payment information, personal files, bank account details, and more, which must be shielded from preying eyes in the event of theft or loss of the device. I’ll be talking about encryption and how can we as users use this superb technique to protect our data.

Plaintext: In cryptography, plaintext is the ordinary, readable text from before being encryption into cypher text and is the result of decryption.
Cipher Text: Cipher text is the encrypted text that is unreadable until it has been decrypted to plaintext with a key. It is used to securely send messages over the Internet.
Encryption Key: A key is a piece of information that can encrypt, decrypt, or perform both functions, depending on the type of encryption being used.
But that’s what we discussed last time, then why today too? Well it’s just an introduction, just doing it for the sake of making the article, a good article you see! :D But there’s more to this introduction this time, don’t worry! :D
A cryptography tool is the one which provides various features to help encrypt your data/messages to prevent eavesdroppers to get hold of it. So first I am going to discuss some popular tools used for this purpose with a brief description of them. Then, I’ll talk about TrueCrypt in detail, where to download, how to use, etc.
Cryptography Tools
- Secret Data Manager: It helps computer users to keep their secret files encrypted to protect data from being stolen. It integrates encryption, compression, hiding files and folders, a file shredder, smart open and automatic updates, and intelligent close through an easy Windows-style user interface.
URL - AxCrypt: It is a file encryption software for Windows. It integrates with Windows to compress, encrypt, decrypt, store, send, and work with individual files.
URL - File Waster: FileWaster protects the file from prying eyes with secure encryption technology. It can encrypt and decrypt files while securely wiping the originals, recurse sub-directories, and compress files before encryption.
URL - MAXA Text2Exe: MAXA Text2Exe hides serial numbers, passwords, phone numbers, and everyday notes in a safe place with a 256-bit AES encryption algorithm. It allows for saving text encrypted as an executable file.
URL - PixelCryptor: PixelCryptor offers an easy-to-use wizard to guide users through the process of encryption and decryption.
URL - EncryptOnClick: EncryptOnClick enables keeping data secure. The encryption and decryption method used is 256-bit AES encryption. It will encrypt, decrypt, compress, and decompress files that can also be opened and decrypted using third-party programs like WinZip 9.
URL - Encrypt Files: It is a free desktop computer software that protects your files and folders from unauthorized viewing. Some of its features include encrypting entire folders, shredding original files, and hiding files after encryption.
URL - Zero Footprint Crypt: It allows users to view encrypted files without having to decrypt them to the hard disk. This allows for maximum security as the file remains in its encrypted state on the hard disk (leaving no footprint on the drive). It allows users to choose either “decrypt to file” or “decrypt to memory”.
URL
TrueCrypt
TrueCrypt is free, open-source, disk encryption software for Windows 7/Vista/XP, Mac OS X, and Linux. This implies, virtually all the systems support it! :) TrueCrypt is a software system for establishing and maintaining an encrypted volume (data storage device). Using this tool, data is automatically encrypted or decrypted before it is loaded or saved, without any user intervention.
TrueCrypt Features
- It creates a virtual encrypted disk within a file and mounts it as a real disk.
- It encrypts an entire partition or storage device such as a USB flash drive or a hard drive.
- It encrypts a partition or drive where Windows is installed(pre-boot authentication).
- Encryption is automatic, real-time, and transparent.
- Parallelization and pipelining allow data to be read and written as fast as if the drive were not encrypted.
- The encryption can be hardware-accelerated on modern processors.
- It provides plausible deniability in case an adversary forces you to reveal the password – hidden volume(steganography) and hidden operating system.
Let’s first download TrueCrypt before I tell you how to use various features of this nice software.
Okay, done? Good. Now install! :P I am not including the screens for installing since it is a simple wizard based installation, OK? Now I am considering you have already installed the software and now I’ll tell you how to use it.
- Run TrueCrypt. Select the desired volume to be encrypted and click Create Volume.

- Volume Creation Wizard Window appears.
- Select the Create an encrypted file container option. This option creates a virtual encrypted disk within a file.
- By default, the Create an encrypted file container option is selected. Click Next to proceed.

- In the next step of the wizard, choose the type of volume.
- Select the Standard TrueCrypt Volume(if you have some non-crucial data to be secured) else, Hidden TrueCrypt Volume(If you are scared that the encrypted volume if seen by someone can force you to tell the password).

- Click next to proceed
- Now select the location of the volume and choose where to save the encrypted locker.

- Then select the Encryption options, i.e. the algorithm, etc. and click Next

- Now choose the size of the encrypted volume. Now click Next

- Then choose the volume password

- The volume format option appears. Select the filesystem for your encrypted volume. This can be FAT/NTFS, etc. Set the cluster to default
- Now move your mouse randomly as fats and randomly as you can for around 30 seconds or so. I don’t know what they do, but somehow the encryption keys are better hardened that way. Maybe they take some values of the mouse locations, MAYBE!

- Now click Format

- Now your volume is created at your specified path. The time taken by this creation step depends on the size of your volume and the filesystem type

- Now on the main TrueCrypt Window, click Select File, and choose the path of your encrypted container.
- Now click Mount

- A password prompt would appear. Key-in your password and click OK

- Your encrypted container will be mounted as a volume which you can use in “My Computer”. Just double click the drive and use it like any other volume.
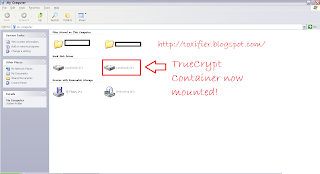
- Once done, select your drive in the TrueCrypt main Window and Click Dismount

Once you dismount your files in the container are saved successfully in the security of true crypt! The best thing is that this tool is completely free and extremely easy to use apart from being just too secure.
Conclusion/Comments
TrueCrypt is a great tool to secure and hide your personal data from other people. You must use it to safeguard your sensitive information.
Today we discussed about a great Cryptography tool and I also listed a few cool ones. I hope you guys download these tools and get your sensitive secure asap!
I hope you find all the relevant information you must know about the topic of security I discussed with you all today. For any queries or suggestions please feel free to comment here. I love to solve problems :D
I hope you all have a great day ahead! :) Happy Tuesday :) See you all soon! :D



No comments:
Post a Comment
Kindly keep the comments clean and make quality comments that would be worthy in making this blog better! :)